CONCISE, PRACTITIONER-
FOCUSED CYBER SURITY
COURSES
A place where aspiring, mid-level, and top-level professionals thrive
CONCISE, PRACTITIONER-
FOCUSED CYBER SURITY
COURSES
A place where aspiring cybersecurity professionals move closer to their goal and thrive.
CONCISE, PRACTITIONER-FOCUSED
CYBER SECURITY COURSES
A place where aspiring cybersecurity professionals move closer to their goal and thrive.
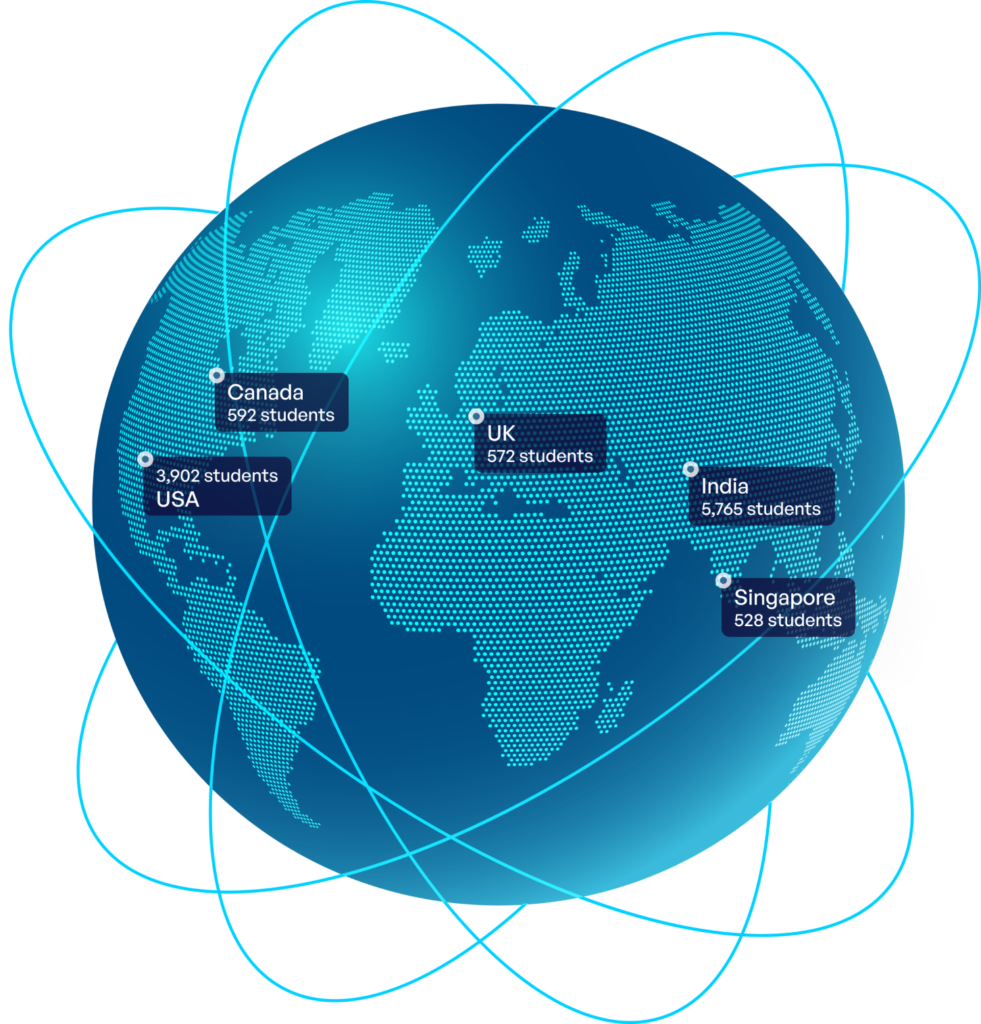
Discover why thousands of learners are partnering with us to help kickstart and advance their cybersecurity careers

Students from around the globe
Cyberation accelerates cyber security career development through practical and relatable courses developed by seasoned professionals
We provide self-paced, instructor-led, and practitioner-focused courses with tools, templates, and a wide array of free resources curated to help you win key cyber defense battles.

Affordable
Our cybersecurity courses are affordable, making high-quality education accessible to all, regardless of budget constraints.

Relatable
We offer relatable content, bridging theory with practical cybersecurity challenges.

Practical
Our training is highly practical, emphasizing hands-on skills and techniques that you can immediately apply in the field.
Concise
Our course materials are concise, focused on delivering essential information efficiently, enabling you to learn quickly and effectively.
Organizations that use our courses to upskill their workforce

Our courses are delivered with the learning preferences of our students in mind
Break into or advance your career in Cybersecurity with us by choosing the course and learning method that work best for you.

Online, Self-paced
Learn at your own pace. From anywhere, at anytime.

Online, Instructor-Led
Learn over a 4-week period, 4-6 hours per weekend

Onsite, Instructor-Led
Learn at our San Antonio, Texas Office (Bootcamp-style)
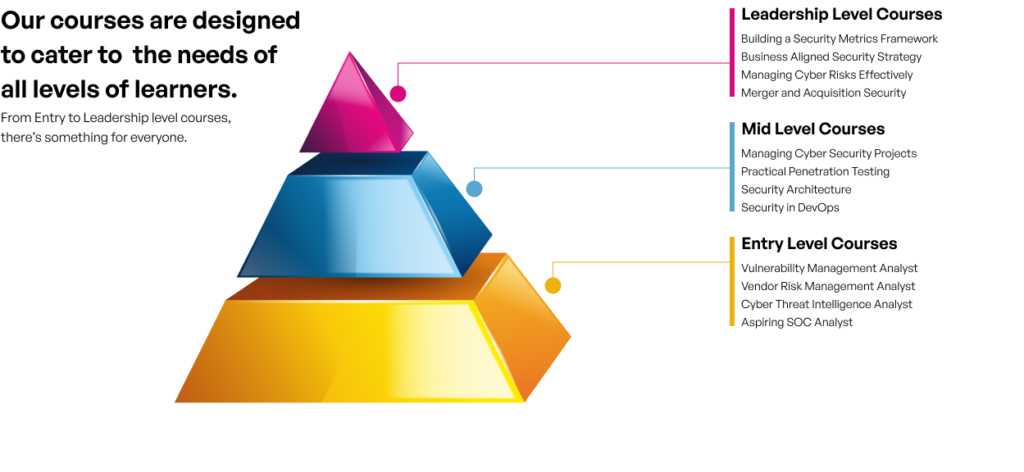
Our Courses
Our courses are designed to cater to the needs of all levels of learners.

Certified SOC Analyst
Join the army of enterprise defenders
Position yourself for an entry-level SOC analyst role with this practitioner-focused course

Certified Cyber Defense Analyst
Join the army of enterprise defenders
Gain the confidence and competence needed to begin your career as a security analyst with broad perspective
Our Courses
Our courses are designed to cater to the needs of all levels of learners.

Entry Level
Discover the exciting world of cybersecurity. Our beginner-friendly courses provide a strong foundation to kickstart your journey with confidence.

Mid-Level
favorably position current IT and
cyber security professionals for their next career move.

Leadership Level
Help other business leaders, company executives, and board members connect the dots from the front defending and supporting organizational goals.

Free Mentorship
Cyber Defense Lab
Ready to enhance your existing skills or gain new ones? Dive into our cyber defense lab to experience what working as a security analyst feels like. Our skill-based scenarios and knowledge-based exercises are designed and developed based on what you are guaranteed to experience in the real-world.

• Skill-based scenario
Researching Suspicious Historical Events
Monitoring security events and responding to events of interest on a near-real time basis is always the most desirable situation. However, this is not always possible especially where an organization lacks adequate human resources...

• Skill-based scenario
Investigating Data Exfiltration Activity
Malicious command execution is one of many important security events to which any security analyst must pay close attention because this is how malicious individuals typically compromise a system or maintain greater control over it...
• Skill-based scenario
Detection and Analysis of Reverse Shell Traffic
A reverse shell allows attackers to bypass network security controls by instructing a compromised computer to initiate outbound communication to an attacker’s machine external to the network....

• Knowledge-based exercise
Data Breach Notification by an External Party

• Knowledge-based exercise
Responding to a Phishing E-mail Storm

Client-Side Attack: Drive by Download
Client-Side Attack: Drive by Download
This carouse will be link to lab page
Immersive Virtual Labs
Ready to enhance your existing skills or gain new ones? Dive into our cyber defense lab to experience what working as a security analyst feels like. Our skill-based scenarios and knowledge-based exercises are designed and developed based on what you are guaranteed to experience in the real-world.

• Skill-based scenario
Researching Suspicious Historical Events
Monitoring security events and responding to events of interest on a near-real time basis is always the most desirable situation. However, this is not always possible especially where an organization lacks adequate human resources...

• Skill-based scenario
Investigating Data Exfiltration Activity
Malicious command execution is one of many important security events to which any security analyst must pay close attention because this is how malicious individuals typically compromise a system or maintain greater control over it...

• Skill-based scenario
Malware Detection, Analysis and Response
Placeholder for body text. Enter text into this container. Body text hugs the contents.

• Skill-based scenario
Investigating Data Exfiltration Activity
Placeholder for body text. Enter text into this container. Body text hugs the contents.
• Skill-based scenario
Detection and Analysis of Reverse Shell Traffic
A reverse shell allows attackers to bypass network security controls by instructing a compromised computer to initiate outbound communication to an attacker’s machine external to the network....

• Skill-based scenario
Investigating Data Exfiltration Activity
Placeholder for body text. Enter text into this container. Body text hugs the contents.
Reviews
Hear what our students are saying about us.
“This course is very nice. In so few
times there were so many concepts introduced and also
well explained. It’s a perfect starting point for those who want
to deepen their knowledge about
cyber security concept,
operations and roles”.

Geogiana BUD
(BELGIUM)
“It was a very informative
overview of the SOC which I will be transferring to soon. Great resources covered and
information was explained clearly
and efficiently.“

Camille J Brown
(USA)
” Excellent course and well-taught.“

James DeVincentis
(USA)
“This course is very nice. In so few times there were so many concepts introduced and also
well explained. It’s a perfect starting point for those who want
to deepen their knowledge about
cyber security concept,
operations and roles”.

PAUL UDOR
(UNITED KINGDOM)
” if you are standing up your own SOC or managing an existing one, I’m sure you will take away many
valuable info that will help make your life easier. “

Mike O’Leary
(USA)
” A video course can be so interesting that i never thought of before attending this one. “

Vijay Kumar D
(INDIA)

